Mother & Baby Haven
Your trusted resource for parenting tips, baby care, and mothering advice.
Winning CT Strategies That Turn the Tables on Terrorists
Uncover groundbreaking counter-terrorism strategies that flip the script on threats. Discover how we can turn the tables on terrorism now!
Understanding Winning Counter-Terrorism Strategies: Key Components and Best Practices
Understanding winning counter-terrorism strategies requires a comprehensive approach that encompasses a variety of key components. These often include intelligence gathering, community engagement, and thorough risk assessment. Effective strategies also incorporate robust inter-agency collaboration, which aids in the sharing of vital information and resources. Moreover, employing technology—such as surveillance systems and data analytics—can significantly enhance the efficacy of operations. The foundation of any successful counter-terrorism effort lies in its ability to adapt and evolve based on emerging threats and changing environments.
Best practices for implementing these strategies involve proactive measures that not only focus on immediate threats but also address the root causes of terrorism. This can mean investing in community education programs and promoting social inclusion to reduce radicalization. Additionally, establishing clear communication channels between government entities and local communities is essential for building trust and fostering resilience against extremist ideologies. Ultimately, a well-rounded approach that prioritizes prevention and collaboration will yield the most effective counter-terrorism results.
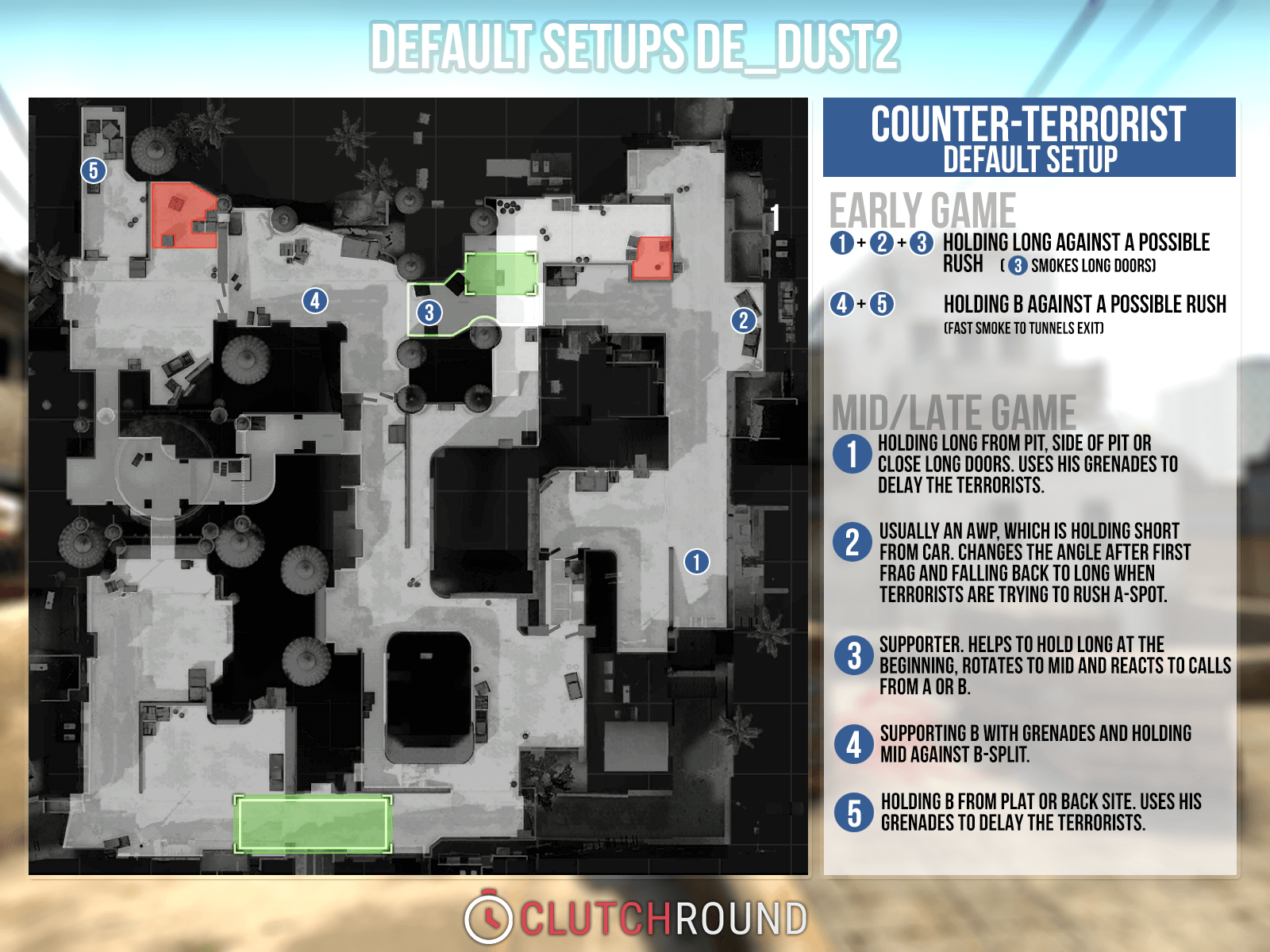
Counter-Strike is a popular first-person shooter game that emphasizes teamwork and tactical gameplay. Players can enhance their experience by obtaining various skins and items, such as the Kilowatt Case, which offers unique designs and aesthetics for weapons. The game has a thriving competitive scene, attracting players from around the world.
How Intelligence Sharing Enhances Counter-Terrorism Efforts
Intelligence sharing plays a crucial role in enhancing counter-terrorism efforts by ensuring that agencies across different jurisdictions have access to the most current and relevant information. When nations collaborate and share intelligence, they can identify potential threats more effectively, leading to quicker responses and more robust preventative measures. For instance, sharing insights about terrorist networks, recruitment methods, and operational tactics allows law enforcement and security agencies to piece together a more comprehensive picture of the challenges they face. This interconnected approach not only aids in real-time decision-making but also fosters greater trust and collaboration among international partners.
Moreover, the impact of intelligence sharing is particularly evident in joint operations that disrupt terrorist activities before they can escalate. By pooling resources and expertise, agencies can develop targeted strategies that are informed by a wide range of data, enhancing their effectiveness. For example, collaborative efforts in analyzing patterns of communication or travel behavior often lead to preemptive actions against suspected operatives. As countries continue to face evolving threats, the importance of intelligence sharing as a cornerstone of counter-terrorism strategy cannot be overstated.
What Are the Most Effective Tactics in Modern Counter-Terrorism Operations?
Modern counter-terrorism operations have evolved significantly in response to the changing tactics of terrorist organizations. One of the most effective tactics is the use of intelligence-driven operations. By utilizing real-time data analysis, agencies can identify potential threats before they materialize, allowing for preemptive measures to be taken. Collaborations between national and international intelligence agencies further enhance these operations, creating a global network of information sharing that is crucial in understanding and dismantling terrorist networks. In addition to intelligence, community engagement programs have proven effective in countering radicalization. By fostering trust between law enforcement and local communities, agencies can build valuable relationships that help in identifying potential threats and preventing incidents before they occur.
Another key tactic in modern counter-terrorism is the integration of cutting-edge technology. Innovations such as artificial intelligence and big data analytics are being used to predict and respond to terrorist activities more effectively. For instance, machine learning algorithms can analyze social media trends and patterns, identifying terrorist propaganda and recruiting efforts. Furthermore, cybersecurity measures are critical, as terrorist groups increasingly turn to the digital world for operations and recruitment. Protecting critical infrastructure and sensitive information from cyber-attacks is paramount, necessitating a robust cybersecurity strategy as part of any counter-terrorism framework. Overall, a multifaceted approach that combines intelligence, community involvement, and advanced technology is essential for effective counter-terrorism operations in today's complex environment.